Total Security Services by CISSP

summary
Threats and Risks in Cyberspace
Cyberspace is a place where new services that bring affluence to people are created one after another, but it is also a place where new information and communication technologies can be easily misused and abused by malicious third parties. These threats can cause damage to the company, such as the following
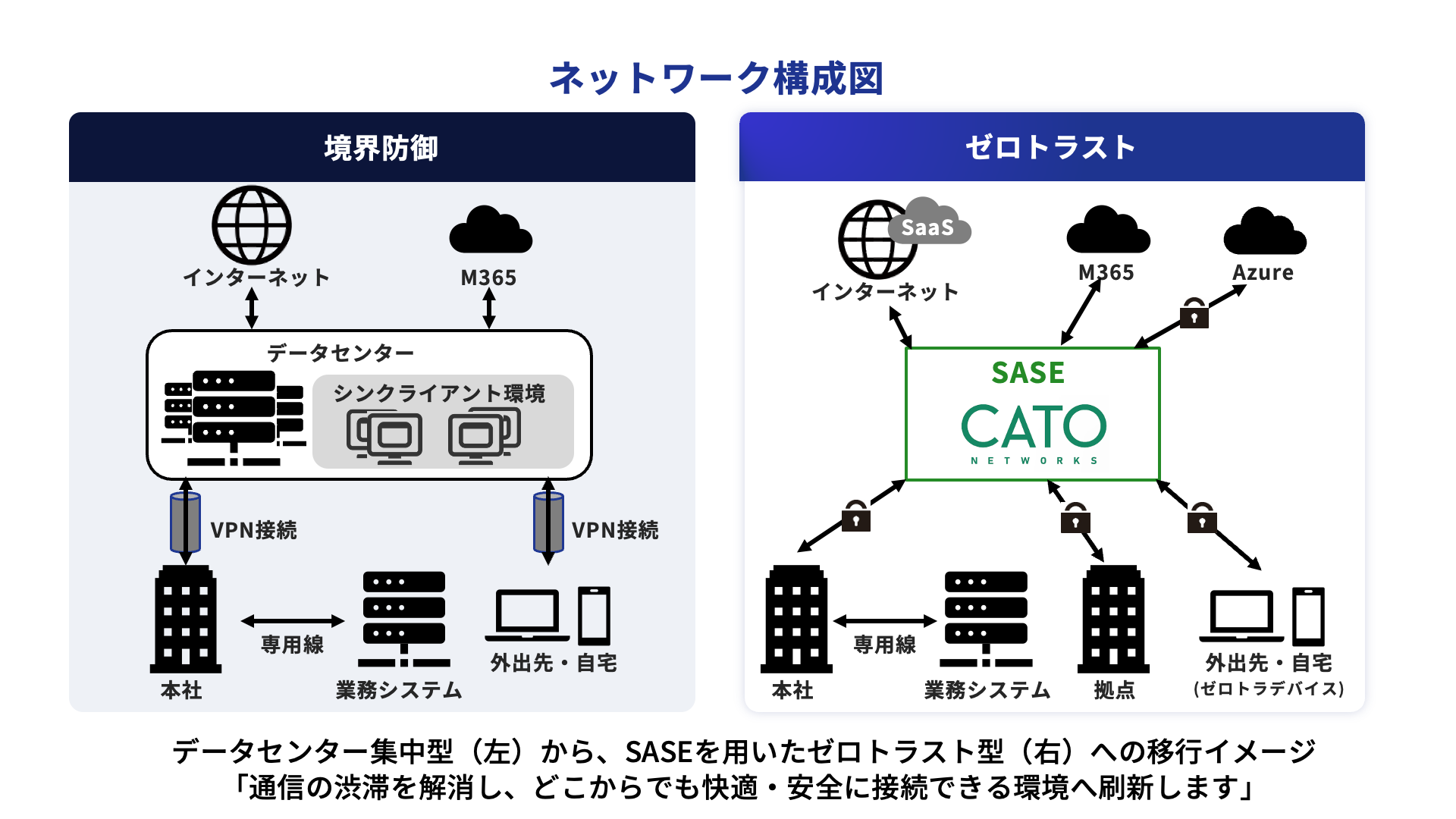
Security Services Offered
Services
TDC SOFT’s portfolio of security services consists of four categories and ten services that are
system lifecycle aware.
Diagnosis and Analysis Analysys
Website and Network Vulnerability Assessment
Reduce the risk of attacks by testing the web and network for vulnerabilities and taking countermeasures.
Penetration Test
System Security Analysis
We will review the design and build status of your system and recommend best practices.

Web application firewall
We can help you build an application firewall tailored to your website’s risks.
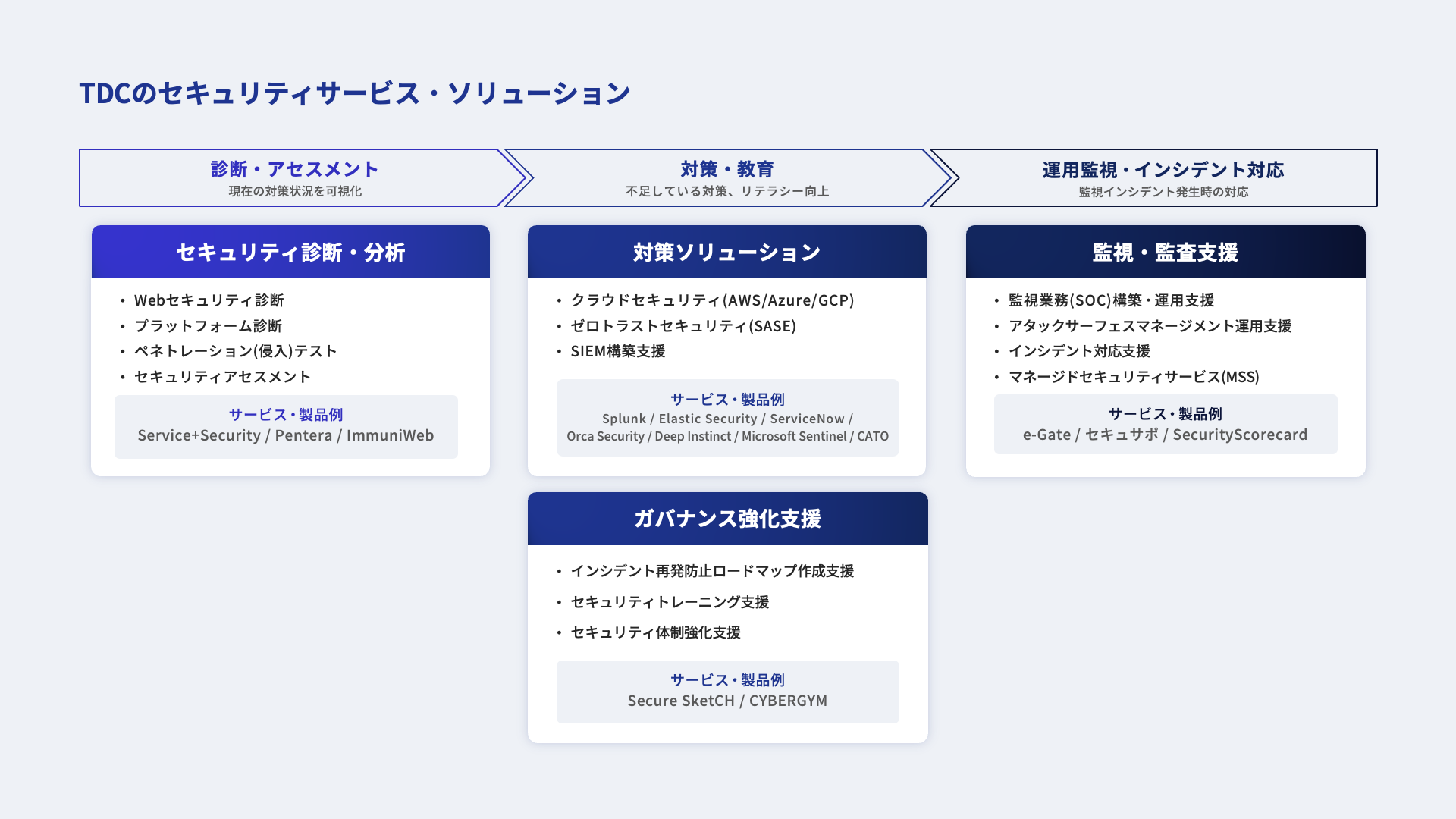
We provide cloud security diagnostics compliant with CIS benchmarks. We also help you build a secure cloud environment based on the diagnosis results.
Container Security
We can propose better solutions for security implementation measures when using containers.
Governance Governance
CSIRT construction support
Security Education Support
Support training to improve employee IT literacy, such as in handling information and responding to targeted e-mail attacks.
Monitoring and Auditing Audit
SIEM, an integrated log analysis platform, is used to support the establishment of a mechanism for early threat detection.
MSS and SOC Support
We provide managed security services (MSS), which include support for the establishment of security operation centers (SOC) and undertaking everything from the installation and operation of security equipment to monitoring and analysis.
Case
Here are some examples of service introductions.
Case 1: System security analysis support
Case 2: Support for building a log analysis infrastructure (SIEM)
Case 3: Advisory on user authentication